Add backend tier status checking to all tier types (#2420)
Moves Tier status check to backend for all Tier types. 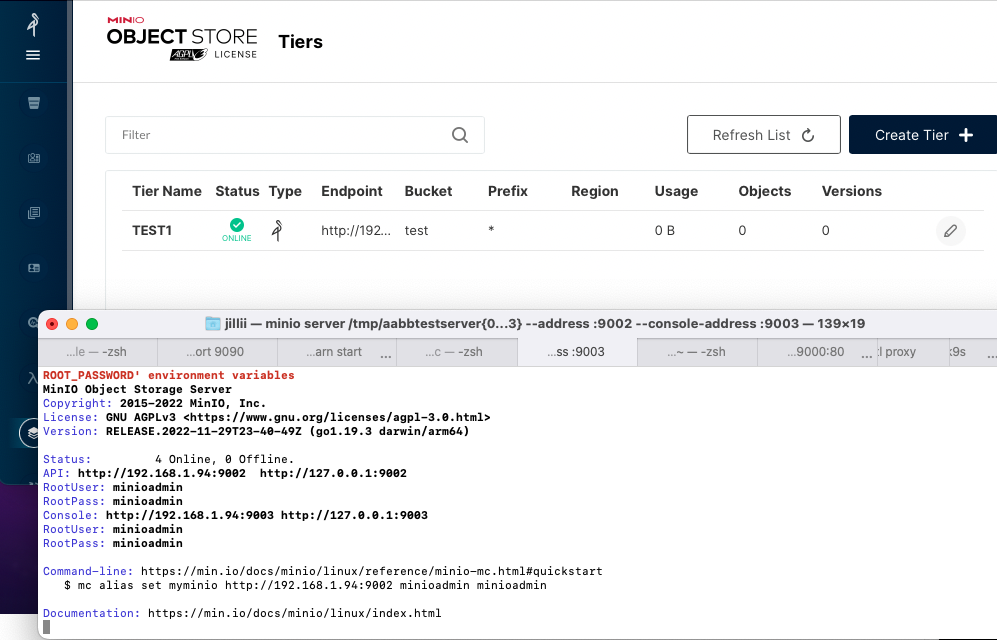 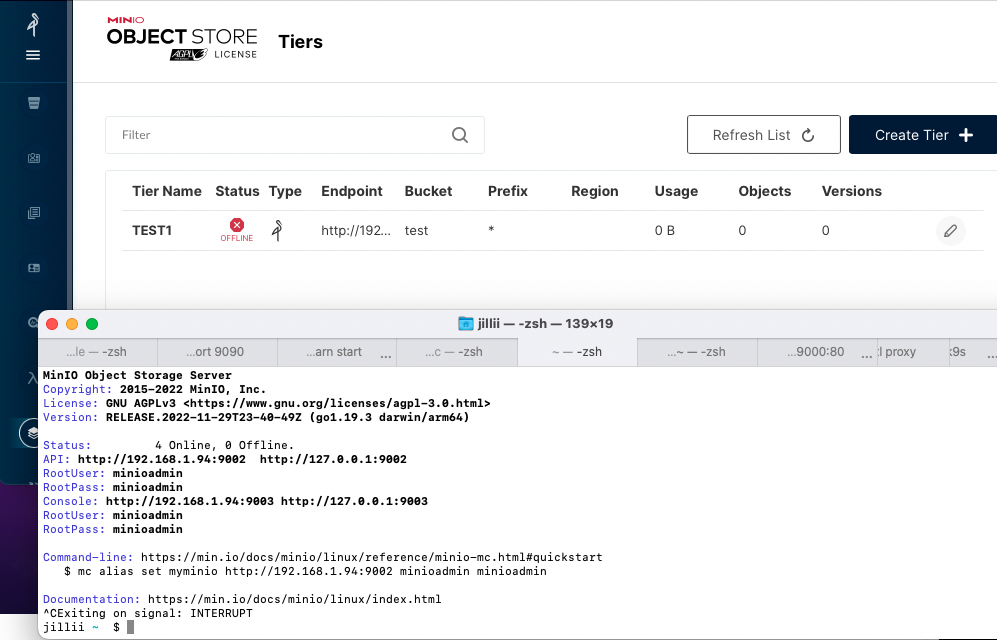 Co-authored-by: Jillian Inapurapu <jillii@Jillians-MBP.attlocal.net> Co-authored-by: Alex <33497058+bexsoft@users.noreply.github.com>
This commit is contained in:
@@ -58,3 +58,8 @@ func (ac adminClientMock) changePassword(ctx context.Context, accessKey, secretK
|
||||
func (ac adminClientMock) speedtest(ctx context.Context, opts madmin.SpeedtestOpts) (chan madmin.SpeedTestResult, error) {
|
||||
return nil, nil
|
||||
}
|
||||
|
||||
// implements madmin.VerifyTier() - WILL ALWAYS RETURN TRUE AS SET NOW, FIX IF USED IN TEST
|
||||
func (ac adminClientMock) verifyTierStatus(ctx context.Context, tierName string) error {
|
||||
return nil
|
||||
}
|
||||
|
||||
@@ -19,10 +19,7 @@ package restapi
|
||||
import (
|
||||
"context"
|
||||
"encoding/base64"
|
||||
"log"
|
||||
"regexp"
|
||||
"strconv"
|
||||
"strings"
|
||||
|
||||
"github.com/dustin/go-humanize"
|
||||
"github.com/go-openapi/runtime/middleware"
|
||||
@@ -30,9 +27,6 @@ import (
|
||||
"github.com/minio/console/restapi/operations"
|
||||
tieringApi "github.com/minio/console/restapi/operations/tiering"
|
||||
"github.com/minio/madmin-go/v2"
|
||||
|
||||
"github.com/minio/minio-go/v7"
|
||||
"github.com/minio/minio-go/v7/pkg/credentials"
|
||||
)
|
||||
|
||||
func registerAdminTiersHandlers(api *operations.ConsoleAPI) {
|
||||
@@ -97,7 +91,6 @@ func getTiers(ctx context.Context, client MinioAdmin) (*models.TierListResponse,
|
||||
break
|
||||
}
|
||||
}
|
||||
|
||||
switch tierData.Type {
|
||||
case madmin.S3:
|
||||
tiersList = append(tiersList, &models.Tier{
|
||||
@@ -115,7 +108,7 @@ func getTiers(ctx context.Context, client MinioAdmin) (*models.TierListResponse,
|
||||
Objects: strconv.Itoa(stats.NumObjects),
|
||||
Versions: strconv.Itoa(stats.NumVersions),
|
||||
},
|
||||
Status: false,
|
||||
Status: client.verifyTierStatus(ctx, tierData.Name) == nil,
|
||||
})
|
||||
case madmin.MinIO:
|
||||
tiersList = append(tiersList, &models.Tier{
|
||||
@@ -132,7 +125,7 @@ func getTiers(ctx context.Context, client MinioAdmin) (*models.TierListResponse,
|
||||
Objects: strconv.Itoa(stats.NumObjects),
|
||||
Versions: strconv.Itoa(stats.NumVersions),
|
||||
},
|
||||
Status: checkTierStatus(tierData.MinIO.Endpoint, tierData.MinIO.AccessKey, tierData.MinIO.SecretKey, tierData.MinIO.Bucket),
|
||||
Status: client.verifyTierStatus(ctx, tierData.Name) == nil,
|
||||
})
|
||||
case madmin.GCS:
|
||||
tiersList = append(tiersList, &models.Tier{
|
||||
@@ -148,7 +141,7 @@ func getTiers(ctx context.Context, client MinioAdmin) (*models.TierListResponse,
|
||||
Objects: strconv.Itoa(stats.NumObjects),
|
||||
Versions: strconv.Itoa(stats.NumVersions),
|
||||
},
|
||||
Status: false,
|
||||
Status: client.verifyTierStatus(ctx, tierData.Name) == nil,
|
||||
})
|
||||
case madmin.Azure:
|
||||
tiersList = append(tiersList, &models.Tier{
|
||||
@@ -165,14 +158,13 @@ func getTiers(ctx context.Context, client MinioAdmin) (*models.TierListResponse,
|
||||
Objects: strconv.Itoa(stats.NumObjects),
|
||||
Versions: strconv.Itoa(stats.NumVersions),
|
||||
},
|
||||
Status: false,
|
||||
Status: client.verifyTierStatus(ctx, tierData.Name) == nil,
|
||||
})
|
||||
case madmin.Unsupported:
|
||||
tiersList = append(tiersList, &models.Tier{
|
||||
Type: models.TierTypeUnsupported,
|
||||
Status: false,
|
||||
Status: client.verifyTierStatus(ctx, tierData.Name) == nil,
|
||||
})
|
||||
|
||||
}
|
||||
}
|
||||
// build response
|
||||
@@ -417,23 +409,3 @@ func getEditTierCredentialsResponse(session *models.Principal, params tieringApi
|
||||
}
|
||||
return nil
|
||||
}
|
||||
|
||||
func checkTierStatus(endpoint string, accessKey string, secretKey string, bucketName string) bool {
|
||||
// Initialize minio client object.
|
||||
re := regexp.MustCompile(`(^\w+:|^)\/\/`)
|
||||
s := re.ReplaceAllString(endpoint, "")
|
||||
minioClient, err := minio.New(s, &minio.Options{
|
||||
Creds: credentials.NewStaticV4(accessKey, secretKey, ""),
|
||||
Secure: false,
|
||||
})
|
||||
if err != nil {
|
||||
log.Println(err)
|
||||
return false
|
||||
}
|
||||
bucketTest, err := minioClient.BucketExists(context.Background(), bucketName)
|
||||
if err != nil {
|
||||
log.Println(err)
|
||||
return strings.Contains(err.Error(), "The request signature we calculated does not match the signature you provided. Check your key and signing method.")
|
||||
}
|
||||
return bucketTest
|
||||
}
|
||||
|
||||
@@ -87,6 +87,7 @@ type MinioAdmin interface {
|
||||
delConfigKV(ctx context.Context, kv string) (err error)
|
||||
serviceRestart(ctx context.Context) error
|
||||
serverInfo(ctx context.Context) (madmin.InfoMessage, error)
|
||||
|
||||
startProfiling(ctx context.Context, profiler madmin.ProfilerType) ([]madmin.StartProfilingResult, error)
|
||||
stopProfiling(ctx context.Context) (io.ReadCloser, error)
|
||||
serviceTrace(ctx context.Context, threshold int64, s3, internal, storage, os, errTrace bool) <-chan madmin.ServiceTraceInfo
|
||||
@@ -116,6 +117,8 @@ type MinioAdmin interface {
|
||||
addTier(ctx context.Context, tier *madmin.TierConfig) error
|
||||
// Edit Tier Credentials
|
||||
editTierCreds(ctx context.Context, tierName string, creds madmin.TierCreds) error
|
||||
// verify Tier status
|
||||
verifyTierStatus(ctx context.Context, tierName string) error
|
||||
// Speedtest
|
||||
speedtest(ctx context.Context, opts madmin.SpeedtestOpts) (chan madmin.SpeedTestResult, error)
|
||||
// Site Relication
|
||||
@@ -462,6 +465,11 @@ func (ac AdminClient) editTierCreds(ctx context.Context, tierName string, creds
|
||||
return ac.Client.EditTier(ctx, tierName, creds)
|
||||
}
|
||||
|
||||
// implements madmin.VerifyTier()
|
||||
func (ac AdminClient) verifyTierStatus(ctx context.Context, tierName string) error {
|
||||
return ac.Client.VerifyTier(ctx, tierName)
|
||||
}
|
||||
|
||||
func NewMinioAdminClient(sessionClaims *models.Principal) (*madmin.AdminClient, error) {
|
||||
adminClient, err := newAdminFromClaims(sessionClaims)
|
||||
if err != nil {
|
||||
|
||||
Reference in New Issue
Block a user